Chain of Custody
Covax utilizes an innovative form of blockchain to create a digital provenance – an immutable auditable record of every time data is touched – for every data molecule. The system uses a series of third-party and intra-system checks to create and validate the chain in a manner that utilizes minimal compute resources with negligible latency.
What is a data molecule?
+A data molecule is the virtual structure that encapsulates the data set. Molecules are highly malleable structures. It doesn’t matter what type of data – block, file, object; structured, unstructured; encrypted or unencrypted – neither does the size or number of files. Access is controlled and tracked at the molecule level.
What is Call Home?
+Call Home is a chain of custody function that protects data that has been removed from the network. When molecules are accessed offline, call home communicates with the home network to update the offline activity into the chain of custody, as well as AI/ML databases.
What type of activity does the chain of custody register?
+The chain of custody registers virtually all activity that impacts your data, its integrity and security. Chain of custody updates when a molecule is created, accessed, data added, data removed, data changed*, copied, data integrity certification performed, moved, deleted, or changes to access protocols.
Artificial Intelligence and Machine Learning
Covax puts the power of artificial intelligence and machine learning on your side. Our AI/ML functionality provides threat detection, access control and validation, and smart policy management.
How does Covax Data threat detection work?
+Our data focused AI/ML draws information from multiple sources, systems and platforms to not just understand what is “normal” but to understand and adapt to what is right.
How does AI/ML help protect data via access control?
+Securing user credentials has long been a vulnerability for networks. Multi-factor authentication was introduced to plug that hole. Even that doesn’t address the full threat issue. By harnessing the power of AI, access is controlled by traditional factors, but also by factors related to behavioral analysis, geographical locations, time-of-day, etc.
What is smart policy management (SPM)?
+Smart policy management is a machine learning function, that, at its core, is designed to bring greater efficiency to your data storage. Secondarily it identifies suspicious behavior. SPM tracks data access, establishing baselines and patterns while comparing that information to existing policies to make recommendations for greater efficiency.
What is object classification and data tagging?
+Object classification and tagging allow you to understand what’s in your data, better track and search your data and identify possible malware and spyware. Object classification is automated, while tagging can be automated and user-driven.
What impact does the AI/ML functionality have on system performance?
+Covax Data maintains the AI/ML databases outside of the normal operating environment. In standard deployments the associated metadata is stored in a Covax Data-owned client database to allow us to harness the power of the Covax Data community. In secure deployments the database is stored in the sterile environment but outside of the operating area.
Deployment and Use
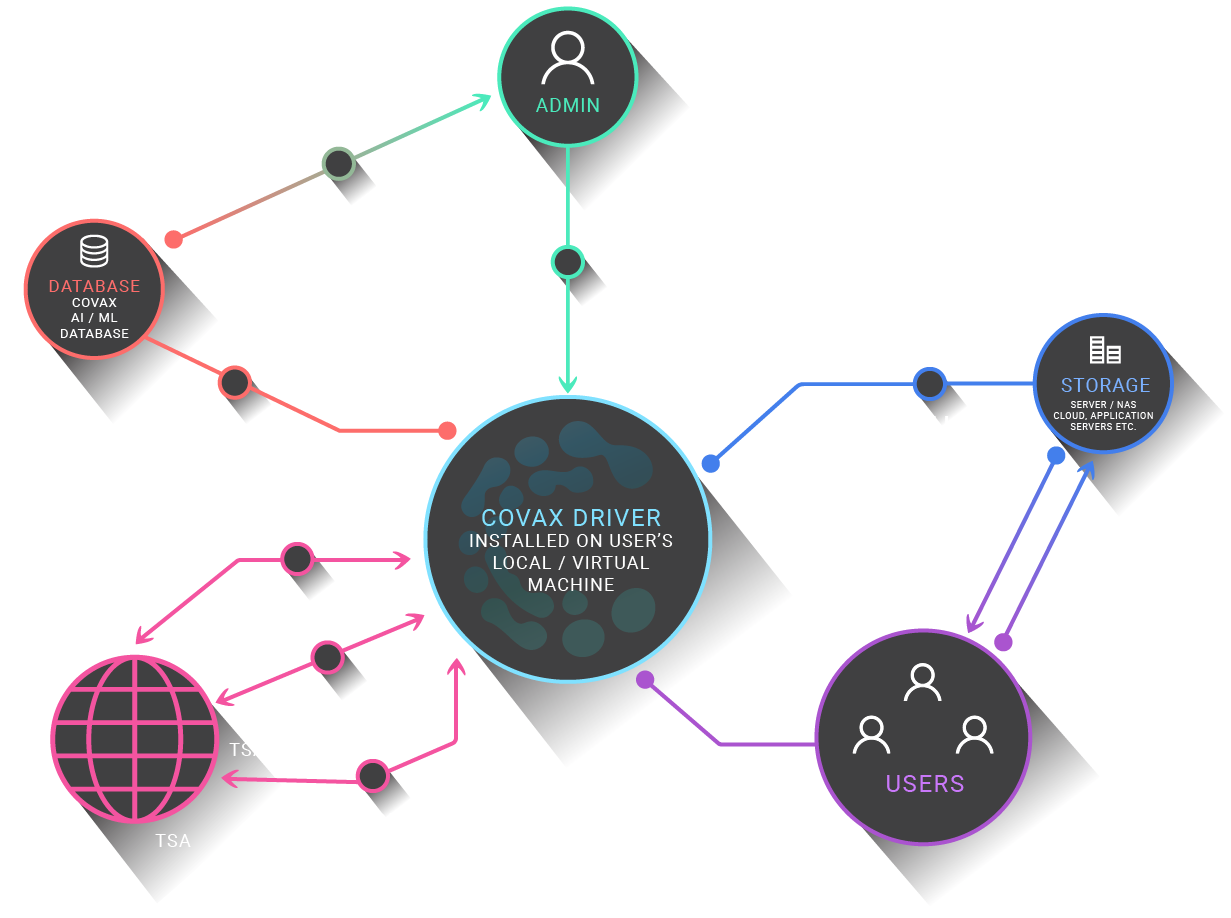
Security and Control Software Solutions by Covax Data
Featuring the next generation blockchain-based integrity and chain of custody solution, ensuring confidence in critical data in the evolving digital world.